Node.Js with Livia || Demystifying User Authentication & Authorization (Part I)
Understanding the concept of Authentication & Authorization
In the world of web applications, ensuring the security of user data and maintaining user privacy is paramount. Two essential aspects of securing web applications are authentication and authorization. These terms might sound similar, but they serve distinct purposes in ensuring that only the right users have access to the right resources. I would be writing a series on this topic where different forms of authentication would be discussed and practical tutorials made available. Meanwhile, In this article, we will dive into the world of authentication and authorization, exploring the concepts, best practices, and implementation strategies to safeguard your application and its users.
User Authentication: Who Are You?

Authentication simply means verification. User Authentication is the process of verifying the identity of a user, ensuring they are who they claim to be. This process typically involves validating user-provided credentials, such as usernames and passwords, against stored records in the application's database. It ensures that a user is who they claim to be before granting access to protected resources.
Authentication asks the question, 'Who are you'. Let’s take a simple analogy to understand this concept better:
Imagine you have a secret clubhouse with a secret password to get in. When your friends/Allies want to come in, you ask them for the password. If they say the right password, you know they are your real friends/Allies and you let them in. This is like how websites and apps ask for a special code (username and password) to make sure you are the right person before letting you use them.
Types of User Authentication
There are several types of authentication spanning from Single Factor Authentication (SFA) to Multi-Factor Authentication (MFA). In this article, I would briefly discuss them and in the subsequent articles, each would be a topic.
Single Factor Authentication (SFA): This is the simplest and most common form of authentication that requires the user to provide only one piece of information to verify their identity. The most common form of SFA is password-based authentication, where the user provides a username and password.
Other types of SFA include:
Token-based authentication: The user is issued a token, which is a small piece of data that contains their identity information. The token is then sent to the server with each request, and the server verifies the token to authenticate the user.
Cookie-based authentication: The user's session ID is stored in a cookie on their browser. The session ID is used to track the user's activity on the website and to verify their identity for subsequent requests.
Biometric authentication: The user's fingerprint, facial scan, or other biometric identifier is used to authenticate them.
Geolocation-based authentication: The user's location is used to verify their identity. For example, a user might only be able to access their account from their home/work IP address, this is majorly used in large organizations.
Multi-Factor Authentication (MFA): This form of authentication requires the user to provide two or more pieces of information to verify their identity. This is in contrast to single-factor authentication, which only requires one piece of evidence, such as a password.
The two or more pieces of evidence used in MFA are typically called factors. The three most common factors are:
Something you know: A password or PIN.
Something you have: A physical token, such as a security key or a mobile device that receives a one-time passcode (OTP).
Something you are: This is a biometric identifier, such as a fingerprint or facial scan.
Single Sign-On Authentication (SSO): This allows users to log in and access multiple accounts and applications using just one set of credentials. SSO can improve security by simplifying username and password management for users, and it makes logging in faster and easier. It can also reduce resetting forgotten passwords.
SSO allows a user to authenticate once with a single identity provider (IdP) and then access multiple applications without having to authenticate again.
💡idP is a service that stores and verifies user identity, they are typically cloud-hosted services and they often work with SSO providers to authenticate users. Examples of SSO providers include; Okta, Auth0, Salesforce and so on.OAuth and OpenID are mostly used to implement SSO.
Passwordless Authentication: This does not require users to enter a password or other knowledge-based authentication factor. Instead, users are authenticated using other factors, such as a one-time password (OTP), a biometric identifier, or a physical token.
Different passwordless authentication methods available include:
One-time passwords (OTPs): OTPs are short, randomly generated codes that are sent to the user's device via SMS, email, or a mobile app.
Biometric authentication: Biometric authentication uses a user's unique physical characteristics, such as a fingerprint or facial scan.
Physical tokens: Physical tokens are small devices that generate OTPs or other authentication codes. The user must enter the code from the token to authenticate themselves.
Passwordless authentication is often used in conjunction with SSO and MFA to improve the user experience, reduce IT administration and complexity, and strengthen security.
Other types of authentication include certificate-based authentication and so on.
User Authorization: What Can You Do?
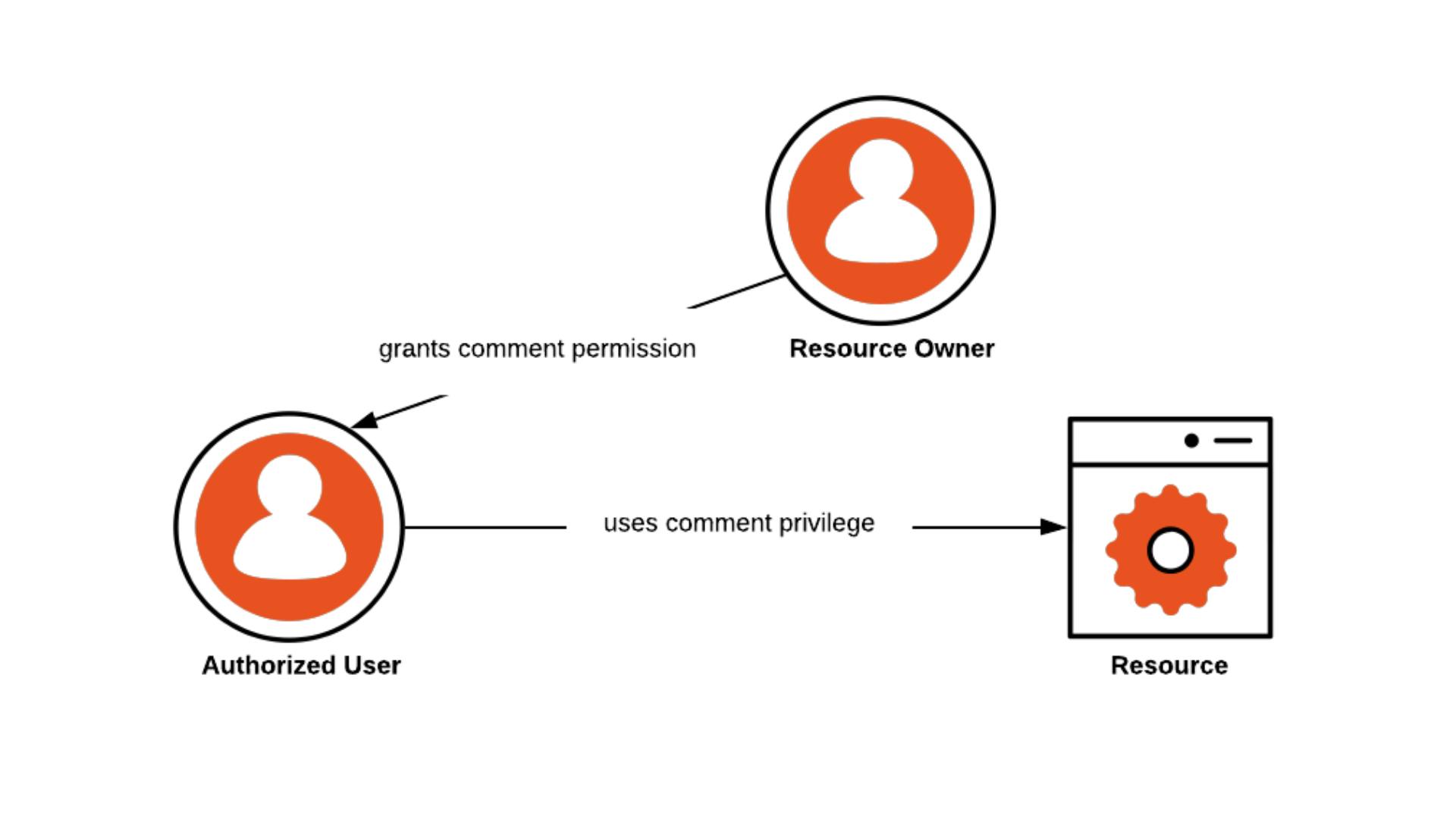
Authorization simply means access. User Authorization deals with what action an authorized user can perform. It restricts access to specific resources or functionalities based on the user's roles, permissions, or other attributes.
Authorization asks the question, 'What can you do' process. Let’s take a simple analogy to understand this concept better:
Remember the secret clubhouse analogy with the password? Well, after your friends come in, you might let some of them read some files or contracts, but not let everyone read everything. That's because you know some friends are good at handling certain contracts or files and which ones might accidentally or intentionally leak secrets or ruin projects. So, just like that, on some websites, even if you have the right password, they might let you do some things, but not everything, because they want to make sure you use only the things you are good at using or you need.
Types of Authorization
There are three main types of authorization methods:
Role-based access control (RBAC): RBAC is a method of authorization that assigns users to roles, and then grants those roles specific permissions. For example, a user with the role of "administrator" might be granted permission to access all resources, while a user with the role of "employee" might only be granted permission to access certain resources.
Just like our Google or one-drive links, we have owners (who created the drive link), viewers(who can only view) and editors(who have access to edit the drive but are not the owners).
Attribute-based access control (ABAC): ABAC is a method of authorization that allows administrators to define permissions based on the attributes of the user or system, such as their role, department, or location. For example, an administrator could define a rule that allows users from the marketing department to access a particular resource, but only if they are located in the United States.
Policy-based access control (PBAC): PBAC is a method of authorization that allows administrators to define policies that determine which users or systems are allowed to access which resources. Policies can be based on a variety of factors, such as the user's role, the resource being accessed, or the time of day.
Conclusion
This article explored the basics of user authentication and authorization, two essential security measures that protect systems and data from unauthorized access. In the upcoming series, I will delve into different authentication methods and give detailed tutorials on how to implement them.
